-

Does a VPN work without Wi-Fi?
A virtual private network (VPN) needs some form of network connection to work, but it doesn’t have to be Wi-Fi. For most people, that means using it over the internet, whether through home broadband...
-

What is Secure Access Service Edge (SASE)?
Traditional security models weren’t built for today’s distributed workplaces. They rely on fixed boundaries and on-premises hardware, which can make it difficult to protect remote users, enforce c...
-

IoT device management: Complete guide
Internet of Things (IoT) devices are everywhere today, from smart home gadgets to medical equipment. While a simple mobile app is usually enough to manage a few devices at home, things get far more co...
-

What is phishing-resistant MFA, and why does it matter?
Multi-factor authentication (MFA) is widely used to keep accounts secure. Traditional MFA methods include one-time passwords (OTPs) sent via email, SMS, or automated voice call, but these can be vulne...
-

What is network discovery? How to enable it safely
When you connect to a new network, your computer often asks if you want your PC to be discoverable. This single click controls network discovery: a function that allows your device to find other devic...
-

IoT cloud security: Threats and best practices
Most Internet of Things (IoT) environments rely on cloud infrastructure to manage device data at scale. However, the size and complexity of these deployments can introduce security gaps that put sensi...
-

What is HTTP/2 and how does it work?
HTTP/2 is a modern version of the Hypertext Transfer Protocol (HTTP) protocol, which manages how browsers and websites exchange data. It was developed to improve the speed and efficiency of web commun...
-

How to open ports on your router
Your router controls how data moves between your home network and the internet. When you open a website, stream a movie, or play an online game, that traffic passes through numbered entry points calle...
-

What is malvertising and how to stay safe online
Malvertising (short for malicious advertising) is when attackers use online ads to spread malware. Instead of hacking websites directly, they hide harmful code inside ads that are delivered through le...
-
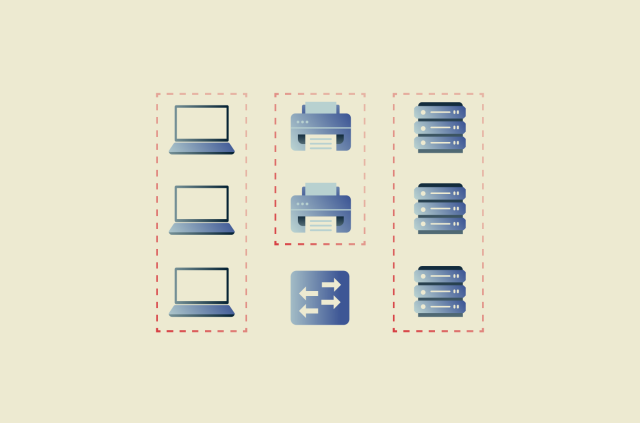
What is a VLAN? A complete guide to virtual LANs
A virtual local area network (VLAN) is a method of segmenting a single physical LAN into multiple separate networks through software. This guide covers how VLANs work, the possible benefits they bring...
Featured





